In recent years, the rise of remote work, online learning, and virtual social gatherings has transformed the way people communicate. One of the most popular platforms for video conferencing is Zoom. However, with the convenience of Zoom comes certain risks, one of which is Zoom bombing. This article explores what Zoom bombing is, how it happens, its consequences, and ways to prevent it.
Understanding Zoom Bombing
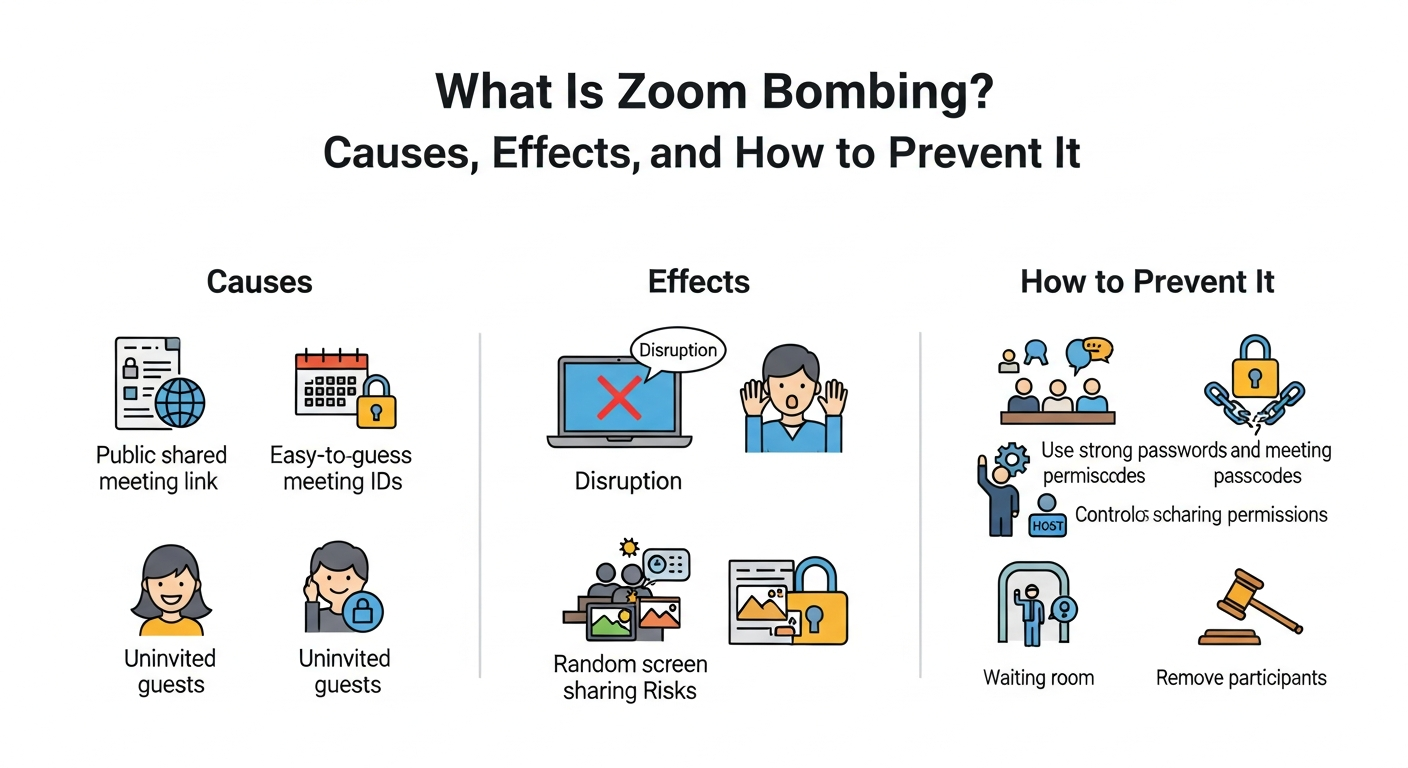
Zoom bombing refers to the unauthorized intrusion of an individual or group into a Zoom meeting. These intruders often disrupt the meeting by sharing inappropriate content, offensive messages, or causing general chaos. The term became widely known during the COVID-19 pandemic, when Zoom usage skyrocketed for business meetings, online classes, and social events.
The motives behind Zoom bombing can vary. Some perpetrators do it for amusement or attention, while others aim to harass or intimidate participants. In some cases, Zoom bombers exploit security vulnerabilities, highlighting the importance of cybersecurity awareness.
How Zoom Bombing Happens
Zoom bombing typically occurs when meetings are not adequately secured. Here are some common ways intruders gain access:
- Sharing meeting links publicly without restrictions
- Using simple or easily guessable meeting IDs
- Skipping passwords for convenience
- Exploiting Zoom’s default settings that allow anyone with a link to join
Once inside, intruders can share offensive images, post inappropriate messages in the chat, unmute participants to make noise, or even take control of shared screens.
The Impact of Zoom Bombing
Zoom bombing can have serious consequences. It may seem like a minor disruption, but its effects can range from embarrassment to serious legal issues. Some impacts include:
- Disruption of professional meetings, causing loss of productivity
- Exposure to offensive or harmful content, affecting mental health
- Compromising confidential or sensitive information
- Legal consequences if explicit or illegal content is shared
- Damage to an organization’s reputation
In educational settings, Zoom bombing can disrupt learning, frighten students, and require significant time to address. In workplaces, it can interrupt operations, reduce employee morale, and create security concerns.
Common Types of Zoom Bombing
Zoom bombing incidents can vary widely depending on the intruder’s intent. Some common types include:
- Prank Bombing: Participants join the meeting to play jokes or make noise without malicious intent.
- Harassment Bombing: Intruders target specific individuals or groups with offensive content or threats.
- Data Breach Bombing: Attackers aim to steal sensitive information or recordings from the meeting.
- Political or Activist Bombing: Groups join meetings to promote a political agenda or disrupt discussion.
Understanding these types can help organizations and individuals better prepare and respond to potential threats.
How to Prevent Zoom Bombing
Prevention is key to keeping meetings secure. Zoom and cybersecurity experts recommend several strategies:
- Use Passwords: Always protect your meetings with strong passwords.
- Enable Waiting Rooms: This allows the host to approve participants before they enter the meeting.
- Limit Screen Sharing: Only allow hosts or specific participants to share their screens.
- Avoid Public Links: Share meeting links privately instead of posting them on social media.
- Update Zoom Regularly: Keep the software up to date to prevent exploitation of security vulnerabilities.
- Lock the Meeting: Once all participants have joined, locking the meeting prevents new intruders.
These steps significantly reduce the risk of Zoom bombing and create a safer online environment for everyone.
Signs Your Meeting Has Been Zoom Bombed
Being aware of the signs can help you quickly address an incident. Common signs include:
- Unexpected participants appearing in the attendee list
- Offensive messages or images in the chat
- Unexplained screen sharing or noise from unknown participants
- Participants being unmuted without permission
- Technical glitches that may indicate unauthorized access
Immediate action, such as removing intruders and reporting incidents to Zoom, is crucial to minimizing the disruption.
Legal and Ethical Considerations
Zoom bombing is not just a nuisance—it can have legal consequences. In many jurisdictions, unauthorized access to online meetings is considered a cybercrime. Sharing explicit content, harassment, or threatening behavior can lead to criminal charges and fines.
Ethically, Zoom bombing violates principles of digital etiquette and respect. It undermines trust in virtual spaces, making it harder for organizations to conduct meetings safely. Organizations and educators have a responsibility to foster secure environments and educate participants about online safety.
Zoom Bombing in Education
Schools and universities were particularly affected by Zoom bombing during the pandemic. Teachers reported disruptions that interfered with lessons, frightened students, and made it challenging to maintain classroom discipline online. Some incidents involved racial slurs or explicit images, highlighting the need for robust security measures in virtual classrooms.
Educators are advised to:
- Set up waiting rooms for each class
- Require students to register with their school email
- Limit screen sharing and chat functions for participants
- Monitor meetings closely and remove intruders immediately
These practices help maintain a safe and productive learning environment.
Zoom Bombing in Business
Businesses also face risks from Zoom bombing. Disruptions during team meetings, client calls, or webinars can lead to embarrassment, lost productivity, and potential leaks of confidential information.
Companies should implement policies that enforce:
- Secure meeting practices for all employees
- Mandatory training on virtual security
- Use of business accounts with enhanced security features
- Reporting procedures for incidents
A proactive approach ensures that employees can collaborate effectively without fear of intrusion.
The Role of Technology in Preventing Zoom Bombing
Technology itself can be a safeguard against Zoom bombing. Zoom continuously updates its platform to address security vulnerabilities. Features such as enhanced encryption, single sign-on (SSO), and AI-based monitoring help reduce risks.
Third-party tools and plugins can also assist in monitoring participant behavior, filtering inappropriate content, and restricting access. Combining technology with strong user practices creates a multi-layered defense against potential threats.
Future of Zoom Security
As virtual meetings become a permanent part of work, education, and social life, Zoom and other platforms are likely to continue investing in security improvements. Biometric authentication, advanced AI moderation, and more customizable access controls are possible future solutions.
Users will need to stay informed about new features and maintain best practices to prevent Zoom bombing. Awareness, preparation, and responsible digital behavior remain the most effective defense.
Conclusion
Zoom bombing is a serious issue that emerged alongside the rise of virtual meetings. While it can be disruptive, embarrassing, and potentially illegal, understanding how it occurs and implementing preventive measures can significantly reduce the risk. By securing meetings, educating participants, and staying vigilant, individuals and organizations can enjoy the benefits of virtual communication without fear of intrusion.